Carlo Alberto Scola
Cyber Security passionate
Security
» categories: security
Cyber Security passionate
» categories: security

How to better protect Docker containers. Tips for increasing the security of your containers for your application and how to run rootless docker containers.

A quick walk-through the basic functions of the Autopsy framework for computer digital forensic and investigations.
categories: #security

How to setup the most simple remote backup solution for your needs. Rsync and EncFS will incrementally store only the encrypted files on your "cloud" providing complete privacy.

The debate on the different vulnerability disclosure options is still running without a decisive winning answer. Cyber Security is not an option for companies but they often seem to not give it much attention.
categories: #security #vulnerability

Subdomain takeover is a threat that comes down to a registration of an unused subdomain by an attacker which is then able to own a valid subdomain and launch different attacks.

Today we are going to explain how to set up a FreeRADIUS server for Authentication, Authorization and Accounting (AAA) along with a MySQL database for credentials storage accessed only through encrypted TLS connections.

The goal is to enable Prestashop SSL/TLS on a NGINX reverse proxy which is acting as SSL/TLS concentrator to an internal non-SSL apache web server.

How to use TOR hidden service with SSH remote tunnel. How to use hidden service as an anonymous SSH proxy. We will set a remote ssh tunnel from a raspi client towards a hidden service,...
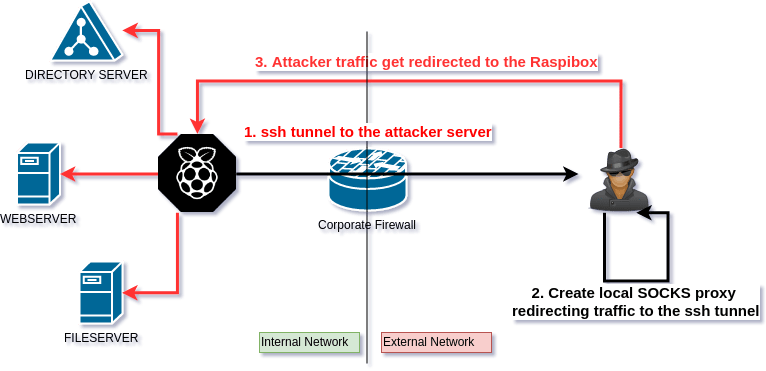
How to set up a SOCKS proxy with SSH reverse tunnel. The tunnel will be ssh-encrypted and each traffic will pass through the tunnel, like in a VPN.
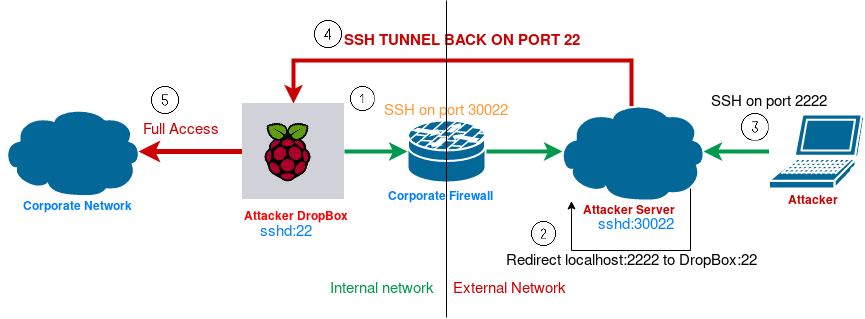
How to set up a persistent, always available, SSH remote tunnel (reverse SSH tunnel).

How to set up SSL/TLS on Apache for securing web communication. Let's Encrypt certificate generation.