SOCKS Proxy through SSH REVERSE TUNNEL
Using only SSH
Last modified: 26 January 2022
How to set up a SOCKS proxy with SSH reverse tunnel. The tunnel will be ssh-encrypted and each traffic will pass through the tunnel, like in a VPN.
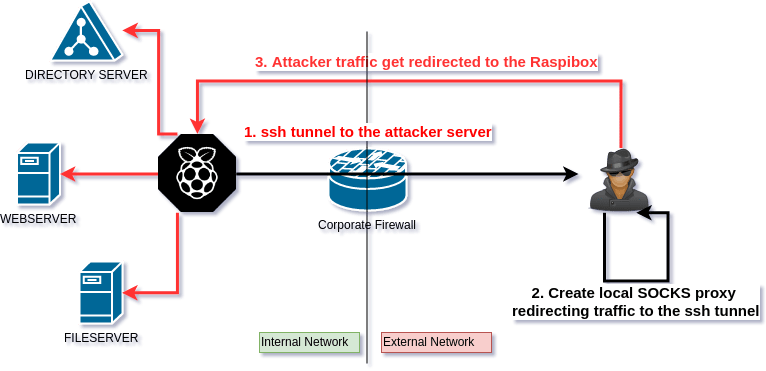
Usually you may need to have an encrypted SOCKS proxy on a network you trust in order to be able to use it whenever you are on a network you don’t trust.
In order to do this you just need to have ssh server active on your remote server, and then just setup a local SOCKS proxy which will redirect traffic through the ssh tunnel.
This is done with:
$ ssh -D 127.0.0.1:12345 -l <remoteuser> -p <remoteSSHServerport> serveruser@domain
Where:
-Dtells ssh to create a local SOCKS PROXY
and SSH will do the rest.
I want to do the opposite
What if the server is a dropbox behind a secure network?
- The dropbox need to connect to the server.
- The server can setup a SOCKS PROXY
- The proxy will redirect traffic through the secure channel
From the dropbox (assume ssh certificate is already copied):
$ ssh -N -R 2222:localhost:22 serveruser@serverdomain
Where:
-Ntells ssh that there will be no commands sent-R [bind_address:]port:host:hostportenable port forward generating a listening socket on port 2222 on the remote server and redirecting it to the local one on port 22
From the server:
$ ssh -D 127.0.0.1:12345 -l <dropboxuser> -p 2222 localhost
Now you can set the proxy on your browser (for example) and packets will be routed to the dropbox.
Please feel free to make any comment! If anything is unclear, just write in the comment and I will update the post!Thanks for reading!
