SubDomain Takeover and how to avoid it.
How to spot unused subdomains
Note, this is a very high level introduction and overview of what a subdomain takeover is, with some examples happened against known websites.
What is DNS Zone Delegation
DNS is a hierarchy structure made of a series of delegations: from the root (.) zone, to (.com) zone (alias Top Level Domain or TLD), to (example.com) zone. How are all the zones linked? Delegation.
In fact the .com delegate the authority of example.com to its own zone.
DNS provide options to divide name-spaces into one or more zones, which can be stored or replicated to others DNS servers. If you want to create additional zones keep in mind:
- Do you want to delegate part of DNS management to another location?
- Do you want to distribute traffic, load balance, have redundancy and ultimately to improve resolutions?
- Do you want to extend name-spaces by adding multiple subdomains at once?
Remember that for each new zone that you create, you need delegation records in other zones that point to the authoritative DNS servers for the new zone.
When a standard primary zone is first created, all the resource record information is stored as a text file on a single DNS server. This server acts as the primary master for the zone. Zone information can be replicated to other DNS servers to improve fault tolerance and server performance.
Subdomain to a new zone

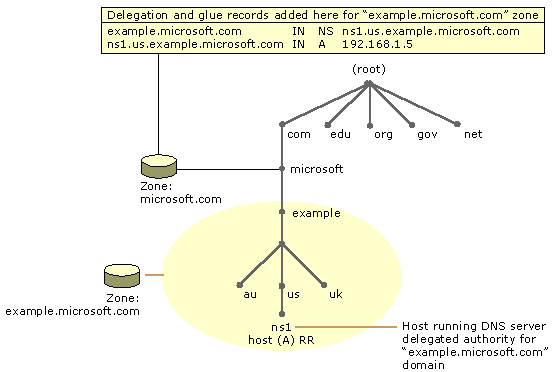
The Figure 1. shows a DNS hierarchy for a new example.microsoft.com domain zone (ns.1.us.example.microsoft.com).
To make authoritative DNS servers know about the new delegated zone, two DNS resource record are required:
- A name-server NS RR to advertise that ns.1.us.example.microsoft.com is an authoritative DNS server for the delegated domain.
- A host (A or AAAA) RR to necessarily resolve the name to its IP address. Ref: https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc771640(v=ws.11)
The Subdomain Takeover
It is considered a high severity threat and boils down to the registration of a domain by somebody else (with bad intentions) in order to gain control over one or more (sub)domains. This attack vector could lead to authentication bypass for example:
Authentication bypass on sso.ubnt.com via subdomain takeover of ping.ubnt.com.
This is not a standard vulnerability, but a chain of two more exotic vulnerabilities leading to a full authentication bypass of your SSO login system at sso.ubnt.com (via account.ubnt.com). The root cause of this authentication bypass is two-fold:
- Subdomain ping.ubnt.com was pointing to Amazon Cloudfront CDN, but the hostname was not registered there anymore. This allowed me to fully takeover this domain. It is now serving content of my own webserver, both over http and https.
- The session cookie of your SSO subdomain sso.ubnt.com is (deliberately?) shared with all https://*.ubnt.com subdomains through its “domain=.ubnt.com” attribute. This allows leakage of this high-value session cookie to the overtaken subdomain https://ping.ubnt.com in all modern browsers.
Scenario
Let’s say a business (e-commerce) is using example.com as primary domain. E-commerce providers (e.g. Shopify, BigCommerce, Magento, Yokart, Big Kartel) will give you a domain for your store like shopexample.ecommerceplatform.com but you want to use your own domain for example shop.example.com. You have two options.
- A 301/302 HTTP redirect from shop.example.com to the domain of the ecommerce platform but will replace the URL in the browser URL bar.
- A CNAME DNS record that delegate DNS resolution directly to the e-commerce provider. Here the URL in the bar remain unchanged.
if one year later you dismiss the subscription, it can happen to forget to update or simply remove the CNAME record in your DNS zone file.
Remove the CNAME record to avoid Subdomain Takeover
When you don’t remove the CNAME record from your DNS zone file, anybody can register a new store in the same e-commerce platform suppliers environment and therefore aim to takeover shop.example.com.
Rule N.1: Check DNS configurations for subdomains pointing at services not in use.
Cloud providers and CDNs
Example. Amazon CloudFront (CDN service) works with the concept of “distributions” (set of static files hosted on the Amazon Cloudfront Edge servers.). After creating a new distribution a new domain name is randomly generated like r42opslbajrw244.cloudfront.net but:
No 1:1 mapping, no dedicated IP address for every distribution but m:n mapping (virtual hosting in Edge servers). HTTP Host Header tells the server which hostname to serve.
If you want to use shop.example.com then a CNAME record like this:
shop.example.com. 600 IN CNAME r42opslbajrw244.cloudfront.net.
with an Alternate Domain Name set on Cloudfront for shop.example.com
WHAT DOES THIS MEAN?
If an attacker can spot a subdomain unused with improper (but still valid) DNS configuration, he can register a new domain with the same name and being pointed to the “takeovered” one. He can trick users to visit the domain as they will not know if they are surfing an illegitimate website, an an attacker can easily steal an authentication cookie.
USA.gov vulnerable to Subdomain Takeover
- suspicious subdomain api.usa.gov with 404 HTTP code
- the api.usa.gov points to CNAME record api-usa-gov.domains.api.data.gov which in turn has A records pointing to AWS servers.
- subdomain not registered in GitHub pages anymore.
Ref: https://blog.sweepatic.com/usa-secured-by-sweepatic/
Subdomain Enumeration
How can we spot subdomains?
Subdomain enumeration is an important part of the reconnaissance phase in the cyber kill chain.
Subdomain enumeration is the process of finding valid (resolvable) subdomains for one or more domain(s). Unless the DNS server exposes a full DNS zone (via AFXR or a “mechanism for replicating DNS data across DNS servers”), it is really hard to obtain a list of existing subdomains.
- dictionary of common names (no strange names)
- crawl second level domain to find links to subdomains (google dorks is faster)
Facebook Certificate Transparency
https://developers.facebook.com/tools/ct
let you subscribe to every change in a domain /subdomain certificate
Tools
DNS Zone Transfer (very uncommon nowadays)
AXFR request directly on the DNS server:
dig @ns.example.com example=.com AXFR
The best practice advises administrators to allow AXFR requests only from authorized DNS servers, so the above technique will probably not work.
NSEC walking attack, which enumerates DNSSEC-signed zones. (https://nmap.org/nsedoc/scripts/dns-nsec-enum.html)
Google Dorks
site:example.com
Rapid7 DNS dataset
https://opendata.rapid7.com/sonar.fdns_v2/ provide a large dataset of domains found on the internet.
To skim and search for:
zcat snapshop.json.gz |
jq -r 'if (.name | test("\\.example\\.com$")) then .name else empty end'
- jq (https://stedolan.github.io/jq/) is like sed for large json data
Or just use —> https://dnsdumpster.com/
Subject Alternative Name
Some tools for finding subdomains:
- Censys.io —> https://censys.io/certificates?q=.example.com
- Crt.sh —> https://crt.sh/?q=%.example.com
- Sublist3r —>
python [sublist3r.py](http://sublist3r.py/) -d [example.com](http://example.com/)
Refs at https://blog.sweepatic.com/art-of-subdomain-enumeration/
More coming soon! Stay cool! and safe ;)
Please feel free to make any comment! If anything is unclear, just write in the comment and I will update the post!
Thanks for reading!
Carlo Alberto
